What will you getting then?
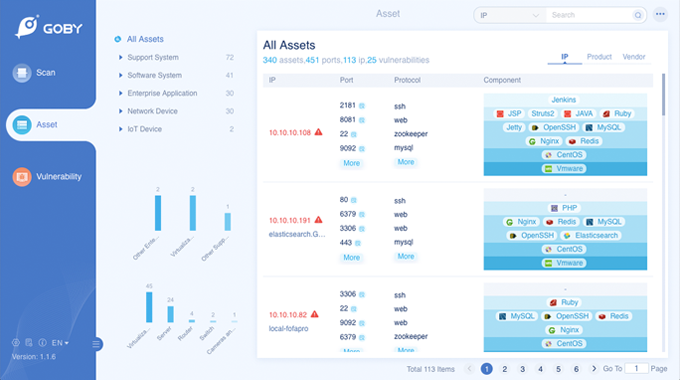
Assets
Generate full assets database
Enjoy
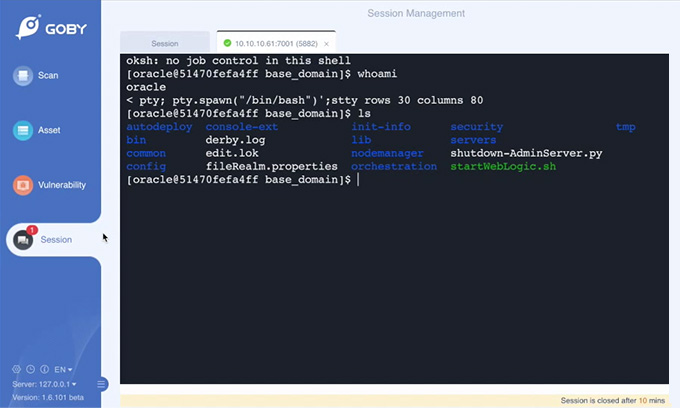
Built for security experts
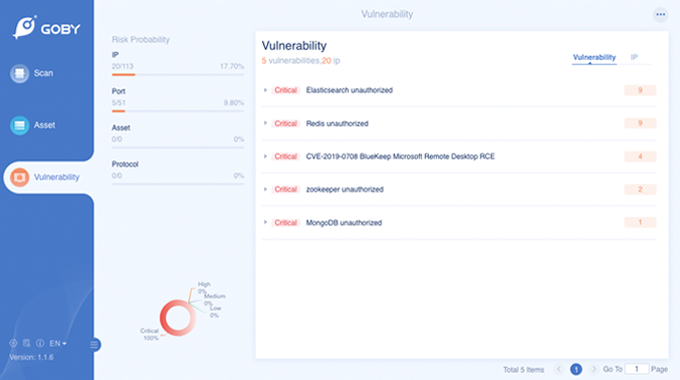
Vulnerabilities
Fastest, check only potentially affected assets
Extensible and customizable
Want even more features? Goby has built-in expansion capabilities. Under the extension API blessing, asset Scanning, vulnerability scanning, themes can be customized or enhanced.
FOFA
ToolsFOFA is a powerful mapping tool for cyberspace assets.
Elasticsearch未授权漏洞利用
ToolsElasticsearch unauthorized vulnerability exploit tool, and supports viewing the Indices information.
Xray
ToolsXray is a web crawler tool.
ZBC
ToolsZoomeye、BinaryEdge、Censys的API。

Shodan
ToolsQuery the IP and ports with Shodan, and support importing JSON files downloaded by Shodan.
SubDomainsBrute
ToolsInput the root domain, brute force subdomain.
Hikvision
ToolsHikvision vulnerability validation tool and returns a snapshot.
Http
ToolsHttp repeater.
RapidDNS
ToolsRapidDNS is a dns query tool which make querying subdomains or sites of a same ip easy!

Super Saiyan
ThemesSuper Saiyan theme.
Goby Professional Benefits

The richest device rule set
More than 100,000 rule identification engines are pre-set in Goby, which can identify and classify hardware equipment and software business system automatically and comprehensively analyze the business system that exists in a network. It currently supports more than 100,000 devices and business systems. Hardware coverage: network equipment, internet of things equipment, network security products, office equipment, etc. Software coverage: CRM, CMS, EMAIL, OA system, etc.

Most lightweight protocol identification
More than 200 protocol identification engines are pre-set in Goby, covering networking protocol, database protocol, IoT protocol, ICS protocol, etc. Through very lightweight Iperf, it can quickly analyze the protocol information corresponding to the port, with fast speed and little impact on target equipment.

Port grouping based on rich attack and defense experience
Our security team summarized the port grouping of different scenarios through the front-line security practice to ensure most efficient output. It is not feasible for penetration test personnel to scan ports 1-65535 on a large network for full coverage, therefore port grouping is particularly important. Currently we have screened over 300 ports for scanning to ensure the highest input-output ratio.

Vulnerability framework based on daily community updates
The vulnerability engine with the most effective attack is pre-set in Goby, covering the critical vulnerabilities such as Weblogic and Tomcat. A large amount of vulnerability information is generated from the Internet (such as CVE) , which are screened and updated on daily basis to identify the ones that would be used for real attacks. Goby also provides a customizable vulnerability checking framework. Security practitioners around the world are motivated to contribute POC to ensure continuous emergency response capability. Meanwhile, We believe that the real-effect-based checks are more valuable than version-based comparisons.

The most comprehensive default password detection
Almost any device will have a default account or even a backdoor account, and the traditional brute force attack mode is not optimal. Pre-set account information of more than 1,000 devices are pre-set in Goby for targeted inspection, ensuring the accuracy and efficiency of risk identification. Goby has built-in brute force attack testing of custom dictionaries for various protocols.
Meet Cyberspace Mapping
The core idea of cyberspace mapping technology is a knowledge base established by first analyzing the rules of the target network IT assets, which is a new technology that can respond in the shortest time in the event of a security incident. Different from traditional port scanning and vulnerability scanning, Goby only deals with certain affected areas in case of a vulnerability incident, resulting in quickest response with the least impact on the target network.
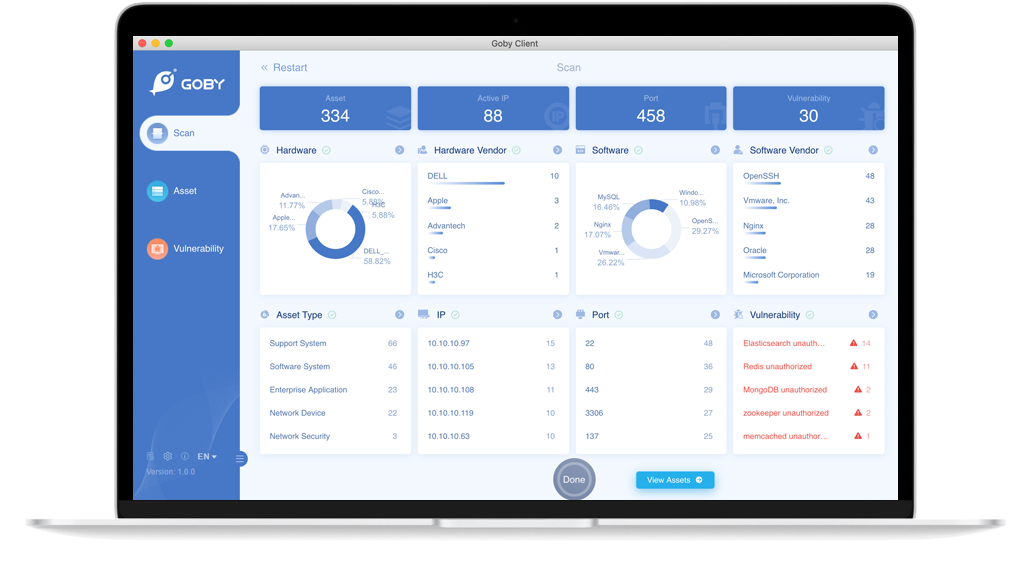
Download Goby
The current Beta of Goby is
Windows
MAC
Linux
Payment Version
More downloads and documentation can be found on the updates page.